12

WSN Authentication using RF Fingerprints (D.
Knox and T. Kunz)


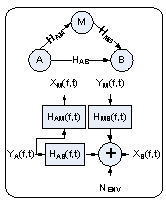
Basic Channel Model
§Attacker
has different radio channels than the one between the legitimate
transmitter and receiver
–Channel differences can be used to advantage by honest nodes
to identify changes in the legitimate channel
–Some
researchers have shown how to extract common random reference
strings from a radio channel
–Channels
are different between other nodes, including non-attacking ones
§Noise:
–Environmental
sources
–Attacker-induced
(e.g. jamming and more subtle types)
–Electrical
and thermal sources inside nodes