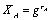15

WSN Authentication using RF Fingerprints (D.
Knox and T. Kunz)


§Objective:
Determine neighbours within RF range and record their RF
Fingerprints and a cryptographic identifier
§Steps:
–Initiator
sends request with a signed nonce and a cryptographic ID of form:
–All
neighbours within RF range acknowledge with their own cryptographic IDs and nonces
§End
Result: Nodes end up with recorded RF Fingerprint values for all of
their neighbours and the corresponding cryptographic identifiers
for each
–‘Neighbours’ must be fully connected with each other and
we assume that a majority of honest nodes exist, permitting
consensus to be reached
Neighbour Discovery with RF Fingerprints