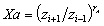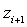16

WSN Authentication using RF Fingerprints (D.
Knox and T. Kunz)


Conference Key Creation (1)
§Objective: Establish confidential
communications between active participants
–Alternatively,
determine a new group of neighbours for which such agreement is possible
1.Initiator calculates a partial
key: xxxxxx
–yyyy is the ID of
the next ‘highest’ neighbour (based on numerical ordering)
2.Initiator
sends partial key and his list of neighbours and their hashed RF Fingerprint
values (hash is a commitment)
–In doing so, the
neighbours of the initiator are provided with a second RF Fingerprint sample,
which they duly note and check for consistency with their first sample.
3.Neighbours
then respond with their own partial keys and their own lists of
neighbours and corresponding hashed RF Fingerprint values
–All neighbours
note each other’s second RF Fingerprint samples and check them for consistency
with their first samples