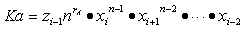17

WSN Authentication using RF Fingerprints (D.
Knox and T. Kunz)


Conference Key Creation (2)
4.The initiator then
generates a (tentative) group of neighbours to be used for the credential and calculates the group shared key as:
5.All other nodes in
the (tentative) group can calculate the same shared key value, provided all parties in the group have been honest.
–Dishonest parties attempting to actively derail the
protocol at this stage must be excluded from the tentative group in a subsequent iteration
6.Steps 1 to 5 are
repeated until a stable group key is established
§Dishonest
parties could participate honestly and then share key values with other dishonest parties.
–The RF fingerprints of the dishonest sharers have been
captured and recorded, inhibiting their ability to assume new cryptographic IDs in other groups
–Trust values for all members of the group in question
decrease when this happens, since anyone of them could have been the ‘mole’ sharing the group’s
secrets.
–RF Fingerprint data is associated with all of the nodes
in question, facilitating their subsequent detection